Switching
VTP
Three VTP modes: server mode; client mode and transparent mode.
Extended VALNs can only be added under the transparent mode.
Trunking
802.1Q by default does not tag the native VLAN. ISL doesn't have native VLAN, it tags all VLANs.
Cisco switches use DTP to negotiate trunk mode and encapsulation mode.
Etherchannel
Two etherchannel negotiation protocols: Cisco's proprietary PAgP and industry standard LACP.
Two switches will form etherchannel with the following modes:
on - on (no PAgP or LACP)
auto - desirable (desirable side initiates PAgP negotiation)
desirable - desirable
active - passive (active side initiates LACP negotiation)
active - active
Connfiguration on all channel member interfaces has to be identical in order to form the etherchannel.
By defult etherchannel load balance base on source addresses. Depending on the traffic pattern, this can be changed to destination based to achieve better load balancing.
Spanning Tree
Spanning Tree has three steps:
1. Select Root Bridge
A bridge ID consists of bridge priority and bridge MAC address. The switch with the lowest bridge ID becomes the root.
2. Select Root Port
Port cost, upstream neighbor's bridge ID, port priority, and port ID are used to select the root port (in that order).
Note: when selecting root port, it is upstream neighbor's port priority that we are comparing. So the port priority affects downstream neighbor, while port cost affects the local switch itself and all its downstream switches, because port cost is accumulative.
3. Select Designated Port
Spanning tree root guard will block a port from which a superior bpdu is received. It may also prevent spanning tree problem when there is a uni-directional fiber failure.
When using spanning tree port-fast, should also enable bpdu guard on the port.
802.1x
Two steps to configure 802.1x:
1. Use aaa authentication dot1x default group radius or tacacs+ in the global mode.
2. on the switch port enter dot1x port-control auto
Private VLAN
Private VLAN, also known as protected ports, is normally used in DMZ. Protected ports cannot communicate with each other, however they can communicate with unprotected ports in the same VLAN.
Switch(config)# interface fastethernet0/1
Switch(config-if)# switchport protected
Port Blocking
It's used to prevent unknown unicast or multicast traffic from being forwarded from one port to another. Port blocking can be configured on a protected or nonprotected port.
Switch(config)# interface gigabitethernet0/1
Switch(config-if)# switchport block multicast
Switch(config-if)# switchport block unicast
Storm Control
Storm control prevents traffic on a LAN from being disrupted by a broadcast, a multicast, or a unicast storm on one of the physical interfaces.
Switch(config)# interface fastethernet0/1
Switch(config-if)# storm-control unicast level 87 65
Switch(config)# interface fastethernet0/1
Switch(config-if)# storm-control broadcast level 20
Port Security
Port security is used to restrict input to an interface by limiting and identifying MAC addresses of the stations allowed to access the port.
Access Control List
Switch ACLs include IP ACLs; MAC ACLs - which can be used to filter non-IP traffic; and VLAN ACLs.
Below is an sample configuration of IP ACL:
Switch(config)# access-list 102 permit tcp any 128.88.0.0 0.0.255.255 gt 1023
Switch(config)# access-list 102 permit tcp any host 128.88.1.2 eq 25
Switch(config)# access-list 102 permit icmp any any
!
Switch(config)# interface gigabitethernet0/1
Switch(config-if)# ip access-group 102 in
And here is the MAC ACL configuration:
Switch(config)# mac access-list extended mac1
Switch(config-ext-macl)# deny any any decnet-iv
Switch(config-ext-macl)# permit any any
!
Switch(config)# interface gigabitethernet0/3
Switch(config-if)# mac access-group mac1 in
Finally the VLAN ACL configuration, remember there is an unexplicit deny any at the end:
Switch(config)# ip access-list extended SERVER1_ACL
Switch(config-ext-nacl))# permit ip 10.1.2.0 0.0.0.255 host 10.1.1.100
Switch(config-ext-nacl))# permit ip host 10.1.1.4 host 10.1.1.100
Switch(config-ext-nacl))# permit ip host 10.1.1.8 host 10.1.1.100
!
Switch(config)# vlan access-map SERVER1_MAP
Switch(config-access-map)# match ip address SERVER1_ACL
Switch(config-access-map)# action drop
Switch(config)# vlan access-map SERVER1_MAP 20
Switch(config-access-map)# action forward
Switch(config-access-map)# exit
!
Switch(config)# vlan filter SERVER1_MAP vlan-list 10-20
Note: VLAN ACL is processed before the router ACL, below is the process flow.
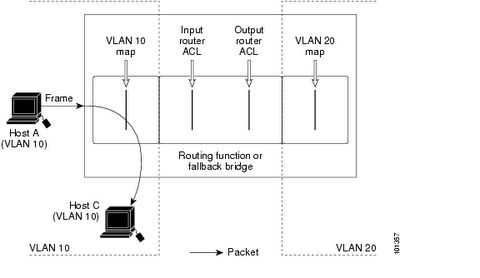
UDLD
UDLD can be used to detect uni-directional fiber problem. UDLD has two modes: enable mode and aggressive mode.
Fallback Bridging
Fallback bridging is to support non-routable legacy protocols across different VLANs.
More information can be found at:
Catalyst 3550 Configuration Guide
